Architecture and Security¶
Architecture¶
-
Single Tenant - Private Cloud Instance ( GC, Azure, AWS )
24/7/365 availability, EU/US/ASIA region deployment options
-
Private Database & private Cloud Storage Bucket Automated Daily Backups
-
Secure
SSL on all clients, Data Encryption, Private Encryption key possible
-
Default Authentication
Token based with SHA256 HMAC signature
-
Enterprise Authentication Options – Single Sign On (SSO)
Microsoft On Premise AD, Azure AD, OAuth 2.0, Google Identity
-
On Premise Deployment Possible
Kubernetes is used as the container based orchestrator
-
Deployment
Kubernetes cluster setup with 4 nodes required
-
Hardware Configuration Master Node reference sample
1 master: Ryzen 3, 8 GB DDR4 RAM, 128 GB SSD
-
Hardware Configuration Worker Node reference sample
3 workers: Ryzen 7, 16 GB RAM, 512 GB SSD
-
Storage
rook and ceph by default, but can be any bucket/object storage supported by K8S
Continuous Delivery¶
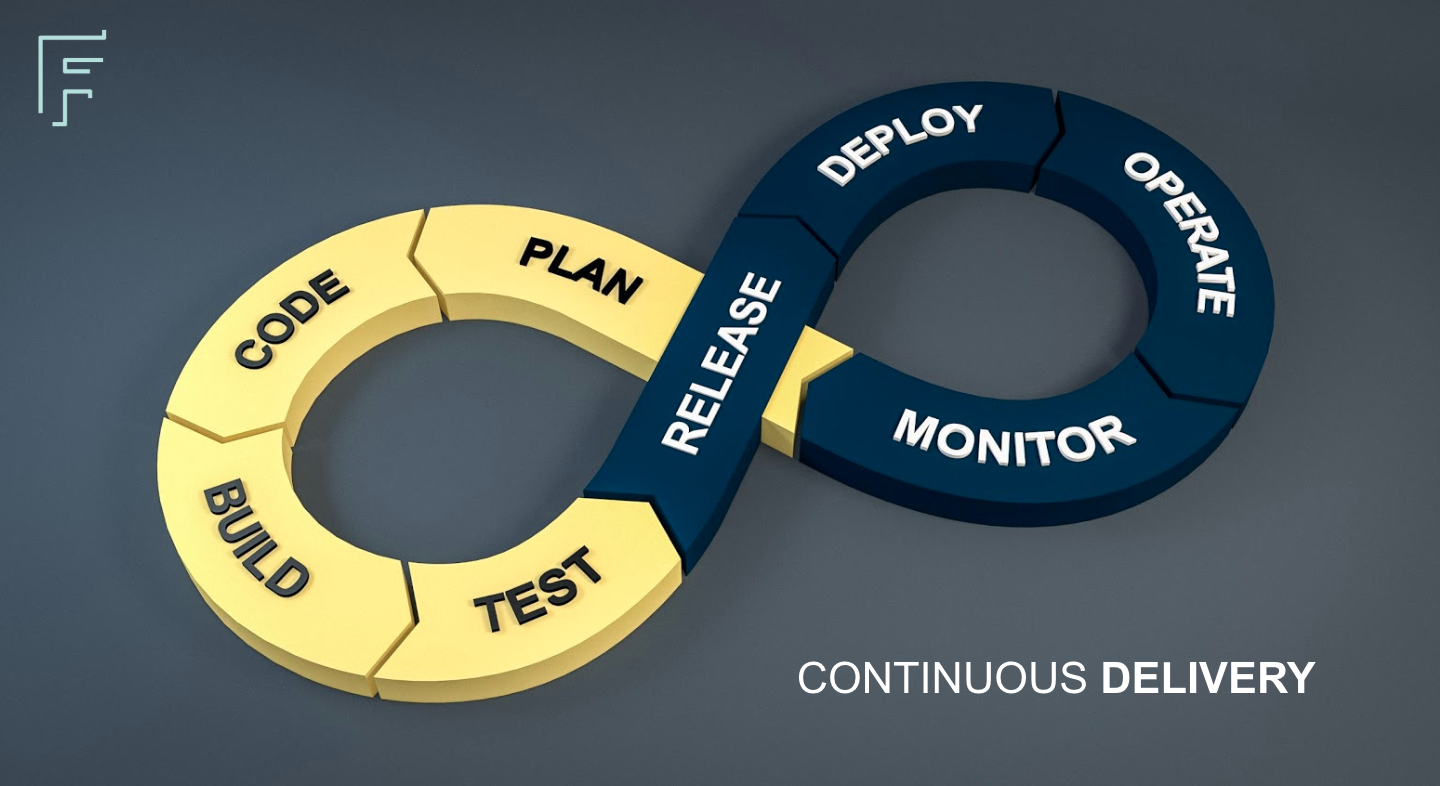
Continuous Integration Workflow¶
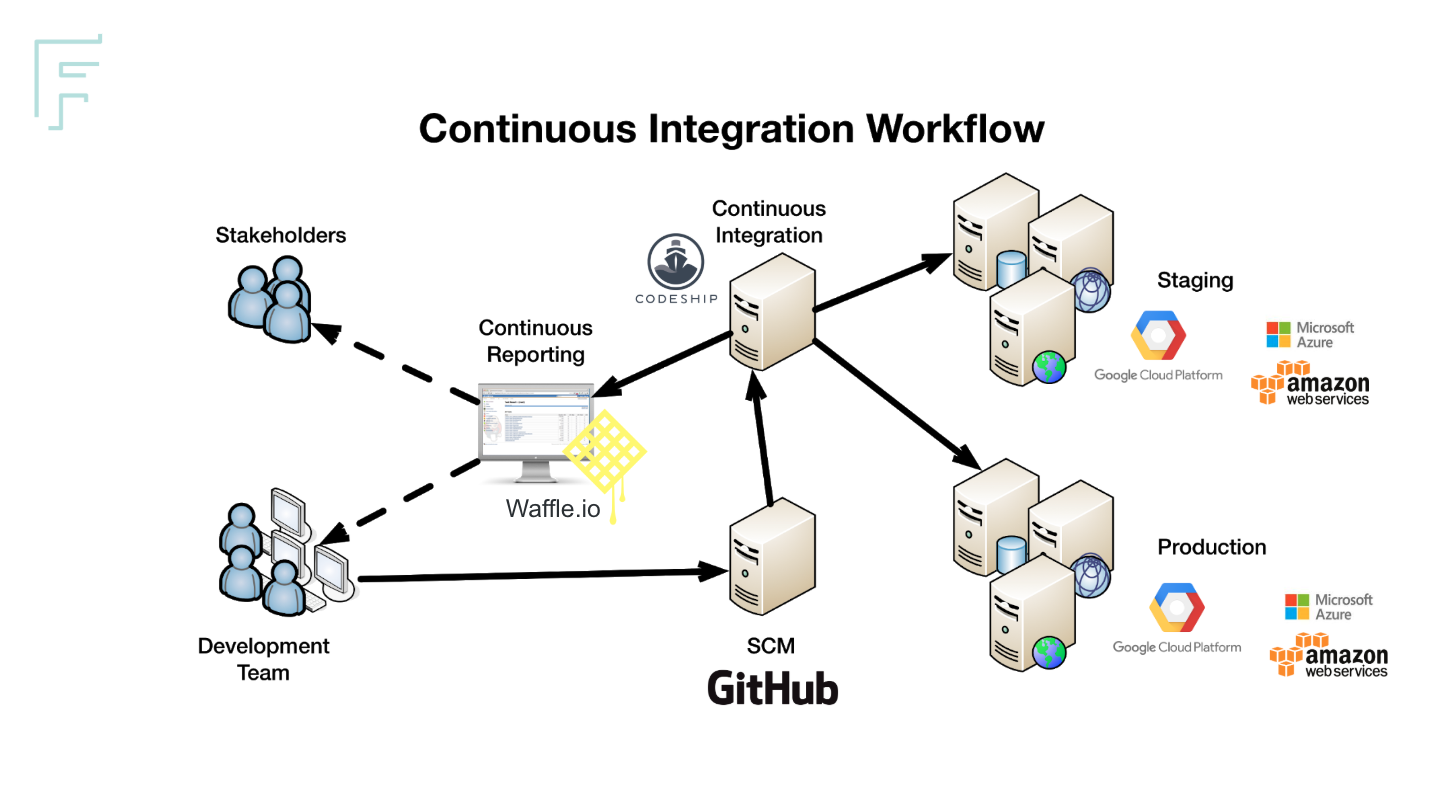
Technology Stack¶

Private Enterprise Container Architecture Diagram¶
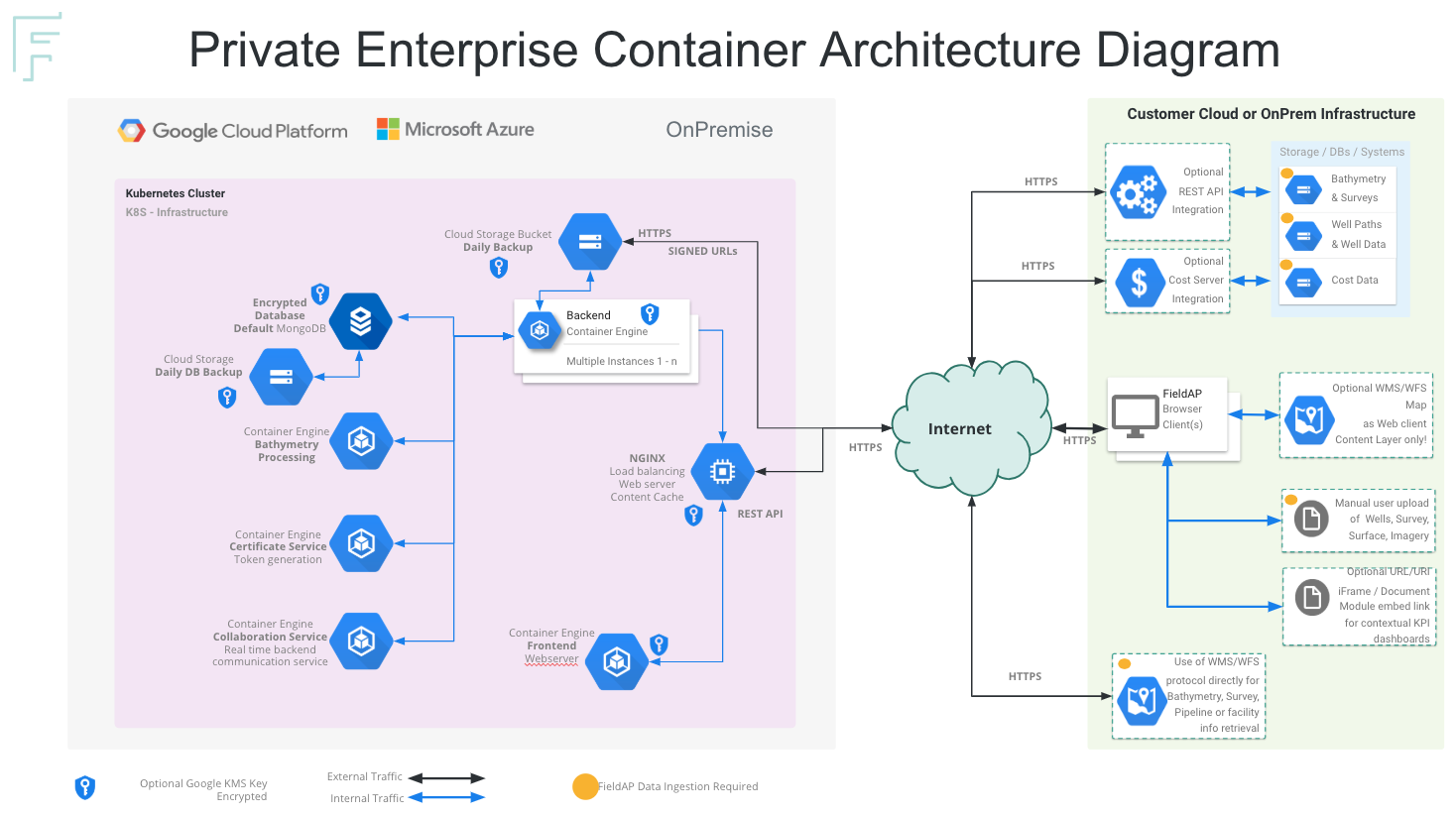
Security & Federation¶
Single Sign On - Requirements¶
-
Identity infrastructure that supports
-
WS-Federation (Passive Requestor Profile)
-
SAML 2.0
-
Fully encrypted communication (HTTPS)
-
Most used supported systems
-
Microsoft Active Directory Federation Services
-
Microsoft Azure Active Directory
-
Email to be setup as a claim in the trust
-
The user’s company email address or other suitable contact email address
-
Claim type: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
-
Requires FieldAP Private Enterprise Space option
Simplified SSO diagram¶
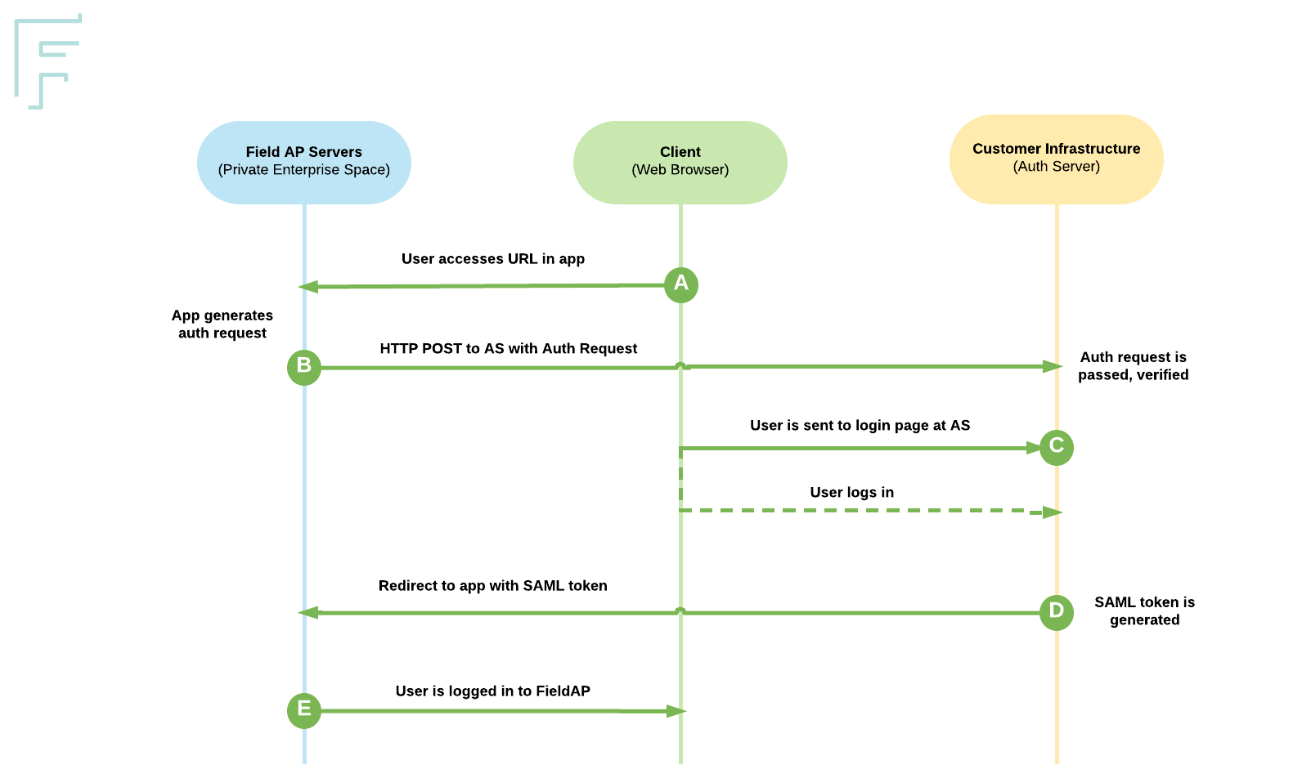
Typical SSO onboarding process¶
-
Customer provides XML metadata for federation
-
The FieldAP Private Enterprise Space is configured
-
FutureOn enables SSO with metadata from customer
-
FutureOn gives the URL for the federation XML metadata to use in the trust configuration
-
The organization sets up the trust based on the XML metadata
-
The SSO is verified and tested
-
Solution is ready to use
Google Cloud Security¶
-
Google Data Centers Certification
-
SSAE16 / ISAE 3402 Type II
- SOC 1
- SOC 2
- SOC 3
- ISO 27001
- ISO 27017
- ISO 27018
-
PCI DSS v3.1
-
Data Encryption
-
Cloud Platform services automatically encrypt data before it is written to disk. For example, the data for each Cloud Storage object is encrypted under the 256-bit Advanced Encryption Standard, and each encryption key is itself encrypted with a regularly rotated set of master keys.
-
Customer Key Management is possible
-
More Information : www.cloud.google.com/security/compliance
MS Azure Cloud Security¶
-
MS Azure Data Centers Certification
-
SOC 1
- SOC 2
- SOC 3
- ISO 27001
- ISO 27017
- ISO 27018
- ISO 9001
- WCAG 2.0
-
and more
-
Data Encryption
-
Azure supports various encryption models, including server-side encryption that uses service-managed keys, customer-managed keys in Key Vault, or customer-managed keys on customer-controlled hardware.
-
More Information : www.microsoft.com/en-us/trustcenter/compliance/complianceofferings